Over 60 million real residential IPs from genuine users across 190+ countries.
Over 60 million real residential IPs from genuine users across 190+ countries.
Your First Plan is on Us!
Get 100% of your first residential proxy purchase back as wallet balance, up to $900.
PROXY SOLUTIONS
Over 60 million real residential IPs from genuine users across 190+ countries.
Reliable mobile data extraction, powered by real 4G/5G mobile IPs.
Guaranteed bandwidth — for reliable, large-scale data transfer.
For time-sensitive tasks, utilize residential IPs with unlimited bandwidth.
Fast and cost-efficient IPs optimized for large-scale scraping.
A powerful web data infrastructure built to power AI models, applications, and agents.
High-speed, low-latency proxies for uninterrupted video data scraping.
Extract video and metadata at scale, seamlessly integrate with cloud platforms and OSS.
6B original videos from 700M unique channels - built for LLM and multimodal model training.
Get accurate and in real-time results sourced from Google, Bing, and more.
Execute scripts in stealth browsers with full rendering and automation
No blocks, no CAPTCHAs—unlock websites seamlessly at scale.
Get instant access to ready-to-use datasets from popular domains.
PROXY PRICING
Full details on all features, parameters, and integrations, with code samples in every major language.
LEARNING HUB
ALL LOCATIONS Proxy Locations
TOOLS
RESELLER
Get up to 50%
Contact sales:partner@thordata.com
Proxies $/GB
Over 60 million real residential IPs from genuine users across 190+ countries.
Reliable mobile data extraction, powered by real 4G/5G mobile IPs.
For time-sensitive tasks, utilize residential IPs with unlimited bandwidth.
Fast and cost-efficient IPs optimized for large-scale scraping.
Guaranteed bandwidth — for reliable, large-scale data transfer.
Scrapers $/GB
Fetch real-time data from 100+ websites,No development or maintenance required.
Get real-time results from search engines. Only pay for successful responses.
Execute scripts in stealth browsers with full rendering and automation.
Bid farewell to CAPTCHAs and anti-scraping, scrape public sites effortlessly.
Dataset Marketplace Pre-collected data from 100+ domains.
Data for AI $/GB
A powerful web data infrastructure built to power AI models, applications, and agents.
High-speed, low-latency proxies for uninterrupted video data scraping.
Extract video and metadata at scale, seamlessly integrate with cloud platforms and OSS.
6B original videos from 700M unique channels - built for LLM and multimodal model training.
Pricing $0/GB
Starts from
Starts from
Starts from
Starts from
Starts from
Starts from
Starts from
Starts from
Docs $/GB
Full details on all features, parameters, and integrations, with code samples in every major language.
Resource $/GB
EN
首单免费!
首次购买住宅代理可获得100%返现至钱包余额,最高$900。
代理 $/GB
数据采集 $/GB
AI数据 $/GB
定价 $0/GB
产品文档
资源 $/GB
简体中文$/GB


As online platforms become more sophisticated at detecting browser fingerprints, managing multiple accounts has shifted from a convenience to a necessity. Today’s websites correlate device, browser, and system signals, not just cookies, to identify linked users.
Professionals, therefore, need isolated browser environments that appear as genuinely separate devices at the fingerprint level. Incogniton was created to address this exact challenge.
Incogniton is a Netherlands-based anti-detect browser with a long-standing presence in the market. Over time, the browser has earned trust by focusing on stability, reliability, and practical workflows rather than experimental features.
This approach has led to adoption by more than 1 million users worldwide, including individuals and companies that manage multiple accounts at scale and cannot afford errors, bans, or data exposure.
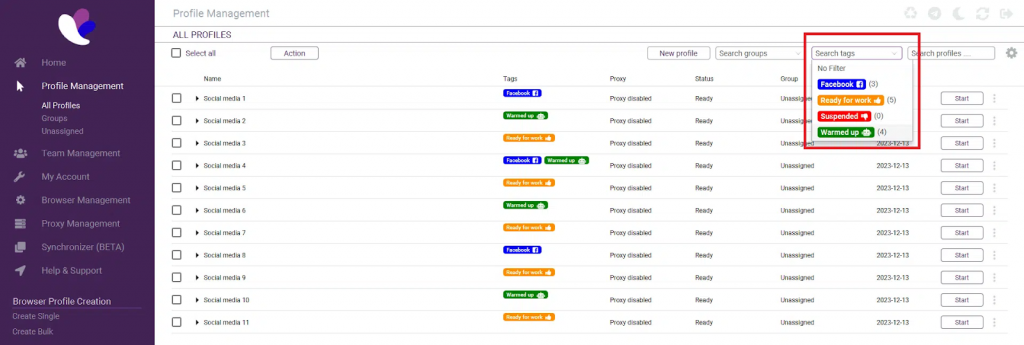
At the core of Incogniton is a browser profile architecture that treats each browser instance as a distinct device. Profiles are generated with consistent, realistic fingerprints derived from low-level signals such as rendering outputs and system characteristics, ensuring each identity remains stable over time and isolated from others.
In practical terms, this means every profile operates with:
● Its own fingerprint configuration
● Separate cookies, cache, and local storage
● Individual proxy and network settings
● Configurable browser versions and system parameters
Because these profiles never overlap, websites see each session as a completely unrelated user. This structure allows professionals to run parallel workflows without the risk of accidental cross-linking.
Many anti-detect tools focus primarily on individual users. Incogniton is designed to support collaborative workflows through role-based team accounts, where access is explicitly controlled.

Team members only see the browser profiles assigned to them, while all profile data, including cookies, fingerprints, and settings, is synchronized through encrypted cloud storage. This allows teams to switch devices or work locations without breaking profile continuity or integrity.
In addition to access control and cloud synchronization, Incogniton includes workflow-oriented tools such as Bulk Profile Creation and the Synchronizer. These tools help teams set up large environments faster and reduce repetitive manual actions.
This design makes Incogniton well-suited for agencies, distributed teams, and organizations that manage shared browser infrastructure at scale.
Incogniton is designed around the assumption that users may be handling sensitive information. The platform operates in alignment with GDPR standards based on its European data handling practices. Privacy and data protection are treated as core requirements within the platform.
By isolating browser data at the profile level and avoiding unnecessary data sharing, Incogniton helps minimize exposure risks. This makes it a viable option for tasks that demand a higher level of caution, such as:
● Managing cryptocurrency wallets and exchanges
● Performing financial or payment-related operations
● Operating high-value or high-risk online accounts
For users who cannot compromise on security, this privacy-first approach is a decisive advantage.
With the Incogniton browser, every profile can be paired with its own proxy, so each session operates under an independent network identity.
Users may plug in third-party proxies, select an option from the Incogniton Proxy Shop, or make use of the free built‑in unblocked proxies for lightweight tasks such as quick tests or scraping.
This per‑profile network assignment ensures that the IP linked to a browser profile remains consistent with its fingerprint, which helps maintain separation between accounts.
With Incogniton, users can:
● Set a proxy for each profile individually
● Switch or update proxies without rebuilding profiles
● Select from residential, mobile, or datacenter IP options depending on task requirements
● Use in‑built proxies for trial runs or low‑risk operations
This structure supports clean identity segmentation for multi‑account setups and reduces the chance of accounts being linked through IP overlaps.
Incogniton also supports automation workflows through its Python and TypeScript SDKs. Developers can work directly with browser profiles using a documented API that simplifies tasks such as launching sessions, managing cookies, or integrating automation pipelines.
The SDKs connect smoothly with automation frameworks like Playwright, Puppeteer, and Selenium. This allows scripts, bots, or QA tooling to operate inside isolated profiles while maintaining fingerprint consistency.
These capabilities make Incogniton suitable for automation-heavy environments, development teams, and users who want to integrate browser control into their software stacks.
This guide walks you through connecting Thordata proxies to Incogniton so each browser profile runs with a clean, dedicated network identity.
● Go to the Incogniton website and download the application for macOS or Windows.
● Install the app and create an account if you are a new user.
● Open Incogniton and sign in.
● Visit the Thordata homepage and sign in or register.
● Choose a proxy plan, such as Residential, ISP, or Datacenter.
● Copy your proxy access details, including Host/IP, Port, Username, and Password.
● In Incogniton, open Profile Management and create a new profile or edit an existing one.
● Navigate to the Proxy tab in the left panel.
● Select the protocol you intend to use, such as HTTP, HTTPS.
● Enter the proxy address in the format IP:Port.
● Provide your Thordata authentication credentials if required.
● Click Check Proxy to verify the connection, then save or create your profile.
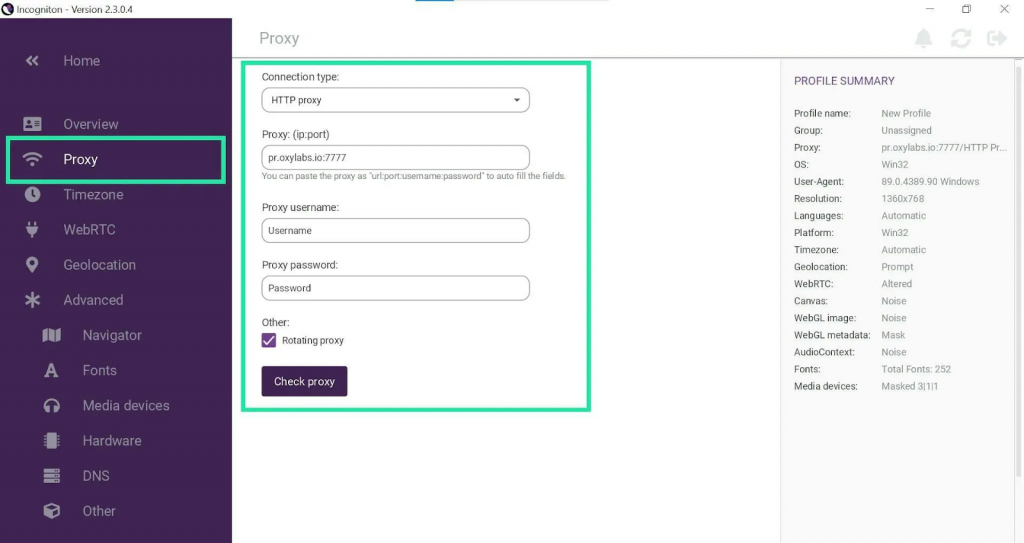
● Start the profile you just configured.
● Visit an IP or geolocation-checking page to confirm the proxy is active.
This setup ensures each Incogniton profile runs with a Thordata-assigned IP, maintaining network separation alongside Incogniton’s isolated fingerprinting system for stable multi-account workflows.
Incogniton has established itself as a dependable anti-detect browser for users who require precision, control, and trust. With its strong profile isolation model, team-oriented design, serious approach to privacy, and robust proxy handling, it stands out as one of the most well-rounded solutions available today.
For professionals working with multiple accounts, especially in environments where mistakes are costly, Incogniton offers a structured, secure, and proven way to operate with confidence.
Contact us at support@thordata.com for tailored advice.
Frequently asked questions
What is Incogniton?
Incogniton is an anti-detect browser designed for managing multiple online accounts securely, using features like fingerprint spoofing to maintain anonymity and avoid detection.
How does it help with multi-accounting?
It allows users to create and manage unique browser profiles, each with customizable digital fingerprints, proxies, and automation tools, making it ideal for tasks like social media marketing or e-commerce.
Is it suitable for beginners?
Yes, its user-friendly interface and automation features make it accessible, though some technical knowledge of proxies helps maximize its potential.
About the author

Jenny is a Content Specialist with a deep passion for digital technology and its impact on business growth. She has an eye for detail and a knack for creatively crafting insightful, results-focused content that educates and inspires. Her expertise lies in helping businesses and individuals navigate the ever-changing digital landscape.
The thordata Blog offers all its content in its original form and solely for informational intent. We do not offer any guarantees regarding the information found on the thordata Blog or any external sites that it may direct you to. It is essential that you seek legal counsel and thoroughly examine the specific terms of service of any website before engaging in any scraping endeavors, or obtain a scraping permit if required.
 Looking for
Top-Tier Residential Proxies?
Looking for
Top-Tier Residential Proxies? 您在寻找顶级高质量的住宅代理吗?
您在寻找顶级高质量的住宅代理吗?
What Is an Open Proxy? Risks of Free Open Proxies
Xyla Huxley Last updated on 2025-01-22 10 min read An o […]
Unknown
2026-02-04

What Is a PIP Proxy? How It Works, Types, and Configuration ?
Xyla Huxley Last updated on 2025-01-28 10 min read […]
Unknown
2026-02-04
TCP and UDP: What’s Different and How to Choose
Xyla Huxley Last updated on 2026-02-03 10 min read […]
Unknown
2026-02-04

Types of Free Proxy Servers Available in 2026
These are raw directories ofte ...
Jenny Avery
2026-02-01

Web Scraping eCommerce Websites with Python: Step-by-Step
This article provides a detail ...
Yulia Taylor
2026-01-29

10 Best Web Scraping Tools in 2026: Prices and Rankings
In this article, discover the ...
Anna Stankevičiūtė
2026-01-29

Best Bing Search API Alternatives List
Discover the best alternatives ...
Anna Stankevičiūtė
2026-01-27

The Ultimate Guide to Web Scraping Walmart in 2026
Learn how to master web scrapi ...
Jenny Avery
2026-01-24
Concurrency vs. Parallelism: Core Differences
This article explores concurre ...
Anna Stankevičiūtė
2026-01-24